How To
Two-Factor Authentication Benefits
Vijay Kakadia
•
Apr 9, 2024
•
5
min read
Share
Hey there, fellow app developer! Are you looking to beef up security for your app users? Well, you're in luck because today we're diving into the world of Two-Factor Authentication (2FA) and why it's a game-changer for app security. Let's break two-factor authentication benefits down in a way even your school pass students can understand!
Introduction to Two-Factor Authentication (2FA)
So, what exactly is 2FA? Imagine it's like having not one, but two locks on your door. It's a security measure that requires users to provide two forms of identification before they can access their accounts. Think of it as an extra layer of protection for your app users' sensitive information.
How Two-Factor Authentication Works
Okay, let's get technical for a second. When a user tries to log in to your app with 2FA enabled, they'll first enter their password (that's lock number one). Then, they'll need to provide a second form of ID, like a unique code sent to their phone (that's lock number two). Only when both locks are unlocked can they get in!
Two-Factor Authentication Benefits
Now, let's talk about the good stuff – the benefits of 2FA for you and your users.
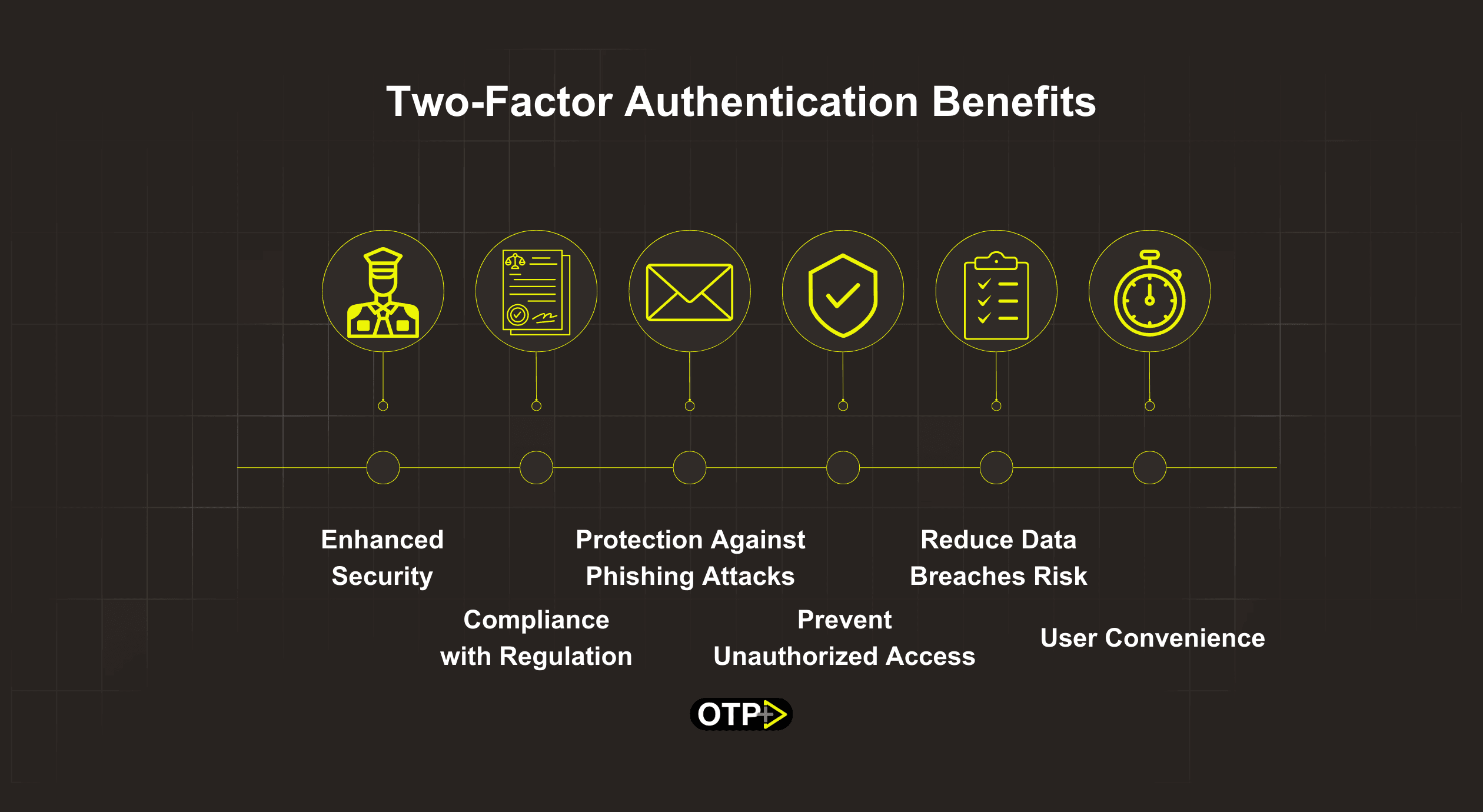
Enhanced Security
One of the primary benefits of 2FA is its ability to significantly enhance security compared to relying solely on passwords. By requiring users to provide two forms of identification before granting access, such as a password combined with a unique code sent to their mobile device, 2FA creates an added barrier for potential attackers. Even if a hacker manages to obtain a user's password, they would still need access to the second authentication factor to successfully breach the account.
Protection Against Phishing Attacks
Phishing attacks, where malicious actors attempt to trick individuals into revealing sensitive information such as passwords, are a prevalent threat in the digital landscape. Two-factor authentication helps mitigate this risk by adding an extra layer of verification beyond what can be obtained through phishing alone. Even if a user unwittingly provides their password in response to a phishing attempt, the attacker would still be unable to access the account without the second authentication factor.
Prevention of Unauthorized Access
2FA serves as a powerful deterrent against unauthorized access to accounts, particularly in cases where passwords may have been compromised through data breaches or other means. By requiring an additional form of verification beyond just a password, 2FA helps ensure that only authorized users can gain entry to sensitive systems and information.
Compliance with Regulations
In many industries, regulatory requirements mandate the use of multi-factor authentication to protect sensitive data and maintain compliance with standards such as GDPR, HIPAA, and PCI DSS. Implementing 2FA not only helps organizations meet these regulatory obligations but also demonstrates a commitment to safeguarding user privacy and security.
User Convenience
Despite providing an added layer of security, 2FA can also enhance user convenience in certain scenarios. Many services offer options such as biometric authentication or authentication apps that streamline the verification process, making it quick and easy for users to access their accounts without sacrificing security.
Reducing the Risk of Data Breaches
Data breaches can have devastating consequences for businesses and individuals alike, leading to financial losses, reputational damage, and legal liabilities. By implementing 2FA, organizations can significantly reduce the risk of unauthorized access to sensitive data, thereby mitigating the potential impact of data breaches.
Real-world Examples of 2FA Implementation
Several high-profile companies and organizations have successfully implemented Two-Factor Authentication to bolster their security posture and protect against unauthorized access. For example, leading tech giants like Google, Facebook, and Apple offer 2FA options such as SMS codes, authenticator apps, and biometric authentication to safeguard user accounts and data.
In addition to tech companies, financial institutions, and healthcare providers also leverage 2FA to protect sensitive information and comply with industry regulations. By requiring customers to verify their identities using multiple factors, banks, insurance companies, and healthcare organizations can enhance security while maintaining user trust and confidence.
Challenges and Limitations of Two-Factor Authentication
While there are many Two-Factor Authentication benefits, it is not without its challenges and limitations. One common issue is user resistance and adoption barriers, as some individuals may find the additional authentication steps cumbersome or inconvenient. Furthermore, certain 2FA methods, such as SMS codes, may be vulnerable to interception or spoofing, potentially exposing users to security risks.
Additionally, implementing and maintaining 2FA systems can incur costs in terms of infrastructure, training, and ongoing support. Organizations must carefully weigh these expenses against the benefits of enhanced security to determine the most effective approach for their specific needs and requirements.
Best Practices for Implementing 2FA
To maximize the effectiveness of Two-Factor Authentication while minimizing potential drawbacks, organizations should follow best practices for implementation and management. This includes:
Choosing the right authentication methods based on security requirements and user preferences
Educating users about the importance of 2FA and providing clear instructions for enabling and using it
Regularly updating security measures and monitoring for any signs of suspicious activity or breaches
By adopting these best practices, organizations can strengthen their security posture and better protect against unauthorized access and data breaches.
Future Trends in Two-Factor Authentication
Looking ahead, the future of Two-Factor Authentication is likely to be shaped by emerging technologies and evolving security threats. Biometric authentication methods, such as fingerprint scanning and facial recognition, are becoming increasingly prevalent and offer a more seamless and secure user experience compared to traditional methods.
Furthermore, context-based authentication, which takes into account factors such as device location, user behavior, and time of access, holds promise for enhancing security while minimizing user friction. By dynamically adjusting authentication requirements based on contextual factors, organizations can better adapt to evolving threats and user needs.
Integration with emerging technologies such as blockchain and artificial intelligence also has the potential to revolutionize the field of authentication, offering new possibilities for securing digital identities and transactions in a decentralized and tamper-resistant manner.
Conclusion
In conclusion, Two-Factor Authentication (2FA) offers a robust and effective means of enhancing online security and protecting against unauthorized access. By requiring users to provide two forms of identification before granting access, 2FA significantly reduces the risk of password-related breaches and phishing attacks, while also providing compliance with regulatory requirements and enhancing user convenience. While challenges and limitations exist, implementing best practices and staying abreast of emerging trends