Tips & Tricks
What is 2FA Authentication?
Vijay Kakadia
•
Mar 22, 2024
•
3
min read
Share
In the world of app development, ensuring robust security is like building a fortress for your digital creations. This is why you need to understand what is 2fa authentication. Two-factor authentication (2FA) is the trusty guard, adding an extra layer of security to your app against hackers.
Our guide breaks down everything about 2FA including the benefits of 2FA, the importance of two-factor authentication, How you can implement it in your app, the criteria for choosing the right 2FA vendor for the application, and the pros & cons of 2FA.
Everything is in a way that even fresh out-of-coding school app developers can grasp.
Before diving into the world of 2FA if you think authentication and authorization same then you should understand the difference between authentication and authorization. Now are you ready for the fly? Alright, lock your seatbelt.
Understanding the Magic Behind 2FA
Alright, let's get the basics down. 2-factor authentication, or 2FA, isn't some tech wizardry. It's like having a double lock on your secret clubhouse. Instead of just knowing the secret key (your password), you also need a special key (something like a code sent to your phone) to get in.
Key Benefits of 2FA
1. Supercharged Security
Think of 2FA as your app's superhero cape. It adds an extra layer of protection, making it way harder for the bad guys to sneak in and mess things up.
2. Protect Against Hackers Attacks
Imagine if your password is a shield. Well, sometimes shields can get stolen. 2FA adds an extra layer to the password, so even if the shield gets swiped, the extra layer stops hackers.
3. Follow the Set of Rules
2FA isn't just a rule; it's your superhero code. It keeps your app in line with data protection rules and regulations.
Importance of Two-Factor Authentication
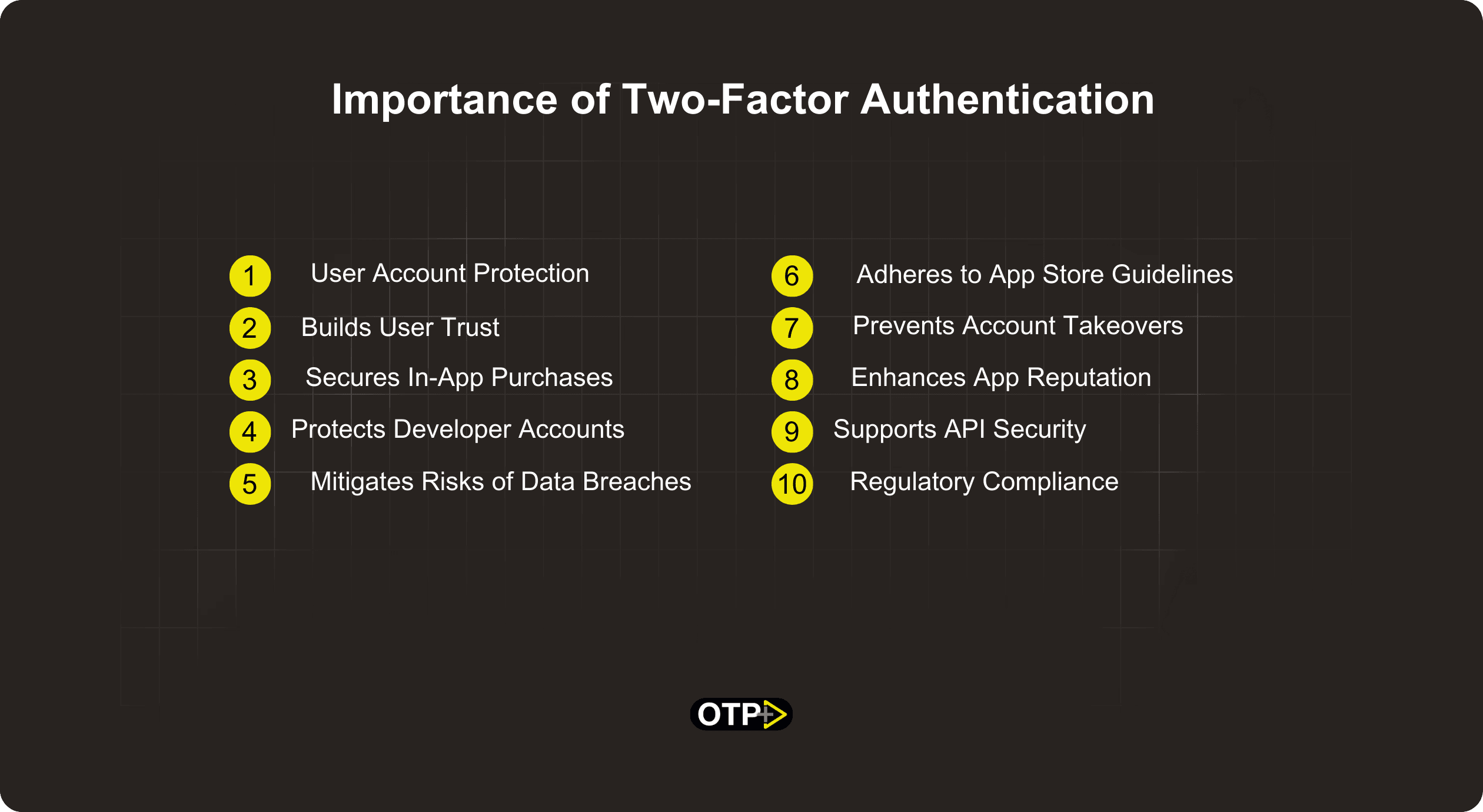
As an app developer, the implementation of two-factor authentication (2FA) holds paramount importance in ensuring the security and integrity of both their applications and the user data they handle. Here's a breakdown of why 2FA is crucial in the context of app development.
1: User Account Protection
You as an App developer, often deal with user accounts that contain personal information, payment details, or sensitive data. Integrating 2FA adds an extra layer of security, reducing the risk of unauthorized access to user accounts.
2: Builds User Trust
Users trust app developers with their information, and security breaches can break this trust quickly. By incorporating 2FA, developers signal a commitment to robust security practices, enhancing user confidence in the app.
3: Secures In-App Purchases
Many apps involve financial transactions or in-app purchases. 2FA safeguards these transactions by ensuring that even if login credentials are compromised, an additional authentication step is required before authorizing any financial activity.
4: Protects Developer Accounts
Developers often have access to sensitive resources and tools related to app development. Implementing 2FA for developer accounts helps safeguard these crucial assets, preventing unauthorized access that could compromise the entire development process.
5: Mitigates Risks of Data Breaches
Usually, Apps handle large amounts of user data, and data breaches can have severe consequences. 2FA acts as a robust defense mechanism, reducing the likelihood of unauthorized access even if login credentials are exposed.
6: Adheres to App Store Guidelines
Some app stores and platforms like Google Play Store and App Store require or strongly recommend the use of 2FA for developer accounts. Adhering to these guidelines not only ensures compliance but also aligns with industry best practices for security.
7: Prevents Account Takeovers
Account takeover attacks are a common threat, where malicious actors gain control of user accounts. 2FA significantly reduces the success rate of these attacks by requiring an additional layer of authentication beyond the username and password.
8: Enhances App Reputation
Security incidents, especially those involving user data, can lose the reputation of an app and its developer. This is why it is important to Integrate 2FA to help maintain a positive image and showcase a commitment to user security and privacy.
9: Supports API Security
Many apps interact with external APIs for various functionalities. Implementing 2FA for API access adds an extra layer of security, preventing unauthorized parties from exploiting API vulnerabilities.
10: Regulatory Compliance
Depending on the app's nature and the regions it operates in, regulatory requirements might mandate the use of strong authentication methods, including 2FA. Adhering to these regulations is crucial for legal and ethical app development practices.
Now you know the importance of two-factor authentication but what about the implementation process? No worries, the next topic is about understanding how you can implement 2FA in your app.
How to Implement 2FA in Your App
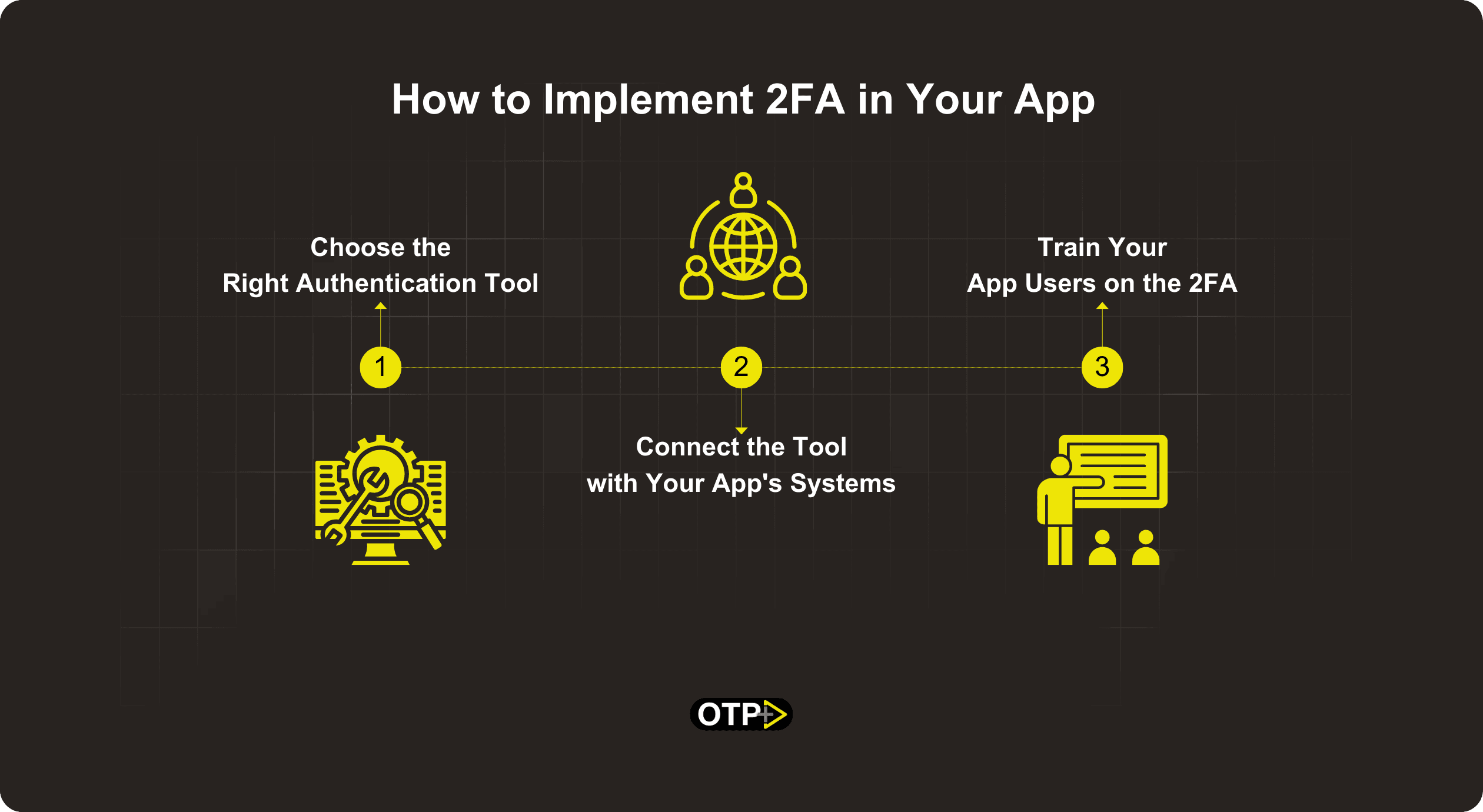
Step 1. Choose the Right Authentication Tools
Choosing the right authentication method is like picking the right tools for your app. You can go for SMS codes, special apps, or even futuristic biometrics. Match the tools to your app's vibe.
Step 2. Connect the Tool with Your App's Systems
Getting 2FA to play nice with your app's systems is crucial. Imagine 2FA as a new character in your app story – it needs to blend in seamlessly. Work with your tech team to make this happen.
Step 3. Train Your App Users on the 2FA
Your app users might need a bit of guidance on this new dance called 2FA. Host cool training sessions, show them the steps, and soon they'll be dancing through the secure login tango.
Criteria to Choose a 2FA Vendor for App Development
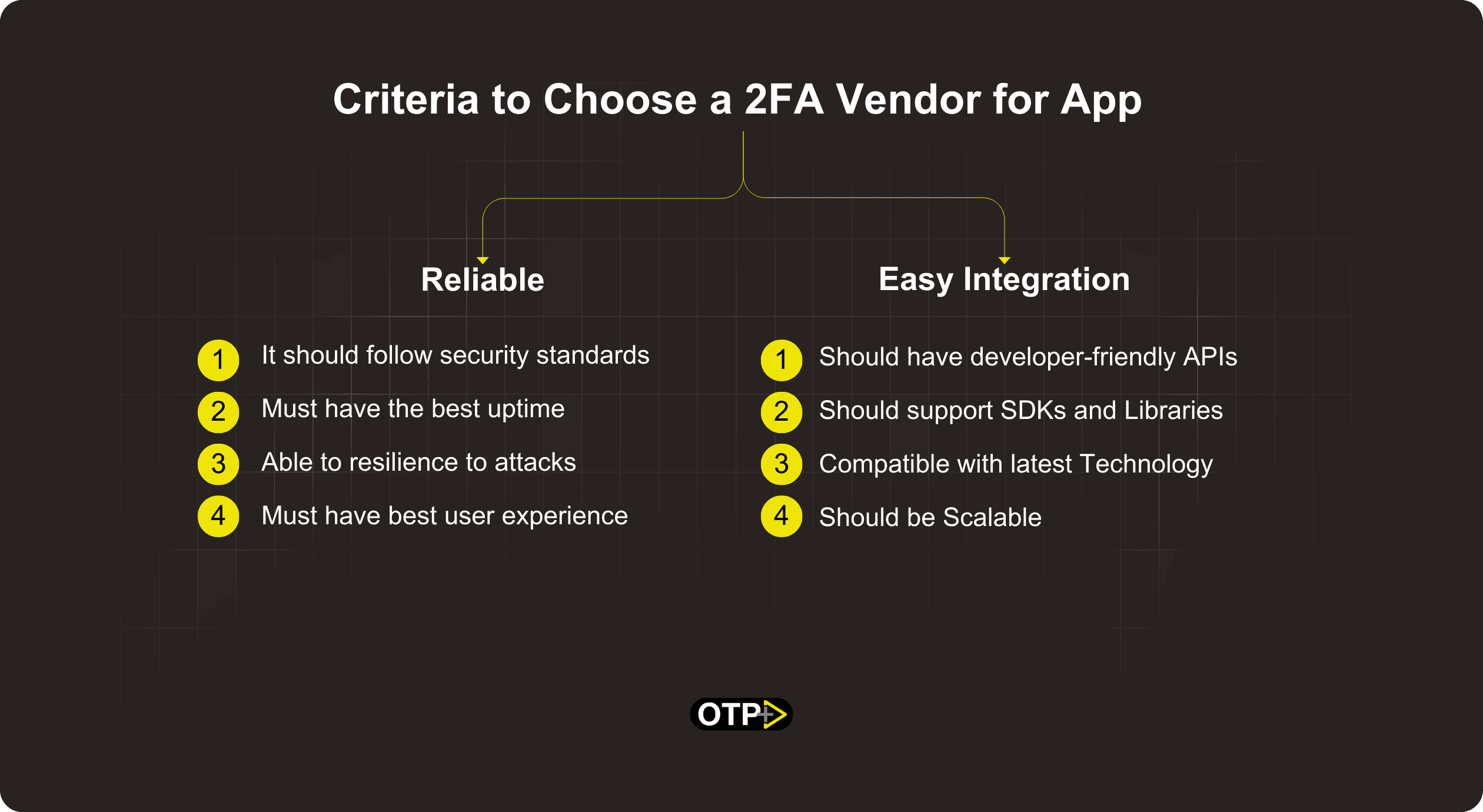
Choosing a Two Way Authentication (2FA) vendor for app development is a critical decision that can significantly impact the security and user experience of your application. Two key criteria to consider in this selection process are reliability and ease of integration.
1: Reliability
Reliability is paramount when it comes to security measures like 2FA. A reliable 2FA vendor should ensure that the authentication process is robust, consistent, and resistant to various forms of attacks. Here are key aspects to consider regarding reliability.
Security Standards
Look for 2FA tools that adhere to industry-standard security protocols. Solutions that comply with standards like OAuth, OpenID Connect, and FIDO (Fast Identity Online) are often more reliable as they have undergone thorough scrutiny and testing.
Uptime and Availability
Choose a 2FA tool with a proven track record of high uptime and availability. It should be capable of handling authentication requests seamlessly, minimizing downtime, and ensuring users can access your application when needed.
Resilience to Attacks
Evaluate the 2FA tool's resistance to common security threats such as phishing, man-in-the-middle attacks, and brute-force attempts. A reliable tool should implement countermeasures to mitigate these risks effectively.
User Experience
While security is important, the 2FA process should not compromise the user experience. Opt for tools that strike a balance between strong security and a user-friendly interface to encourage user adoption.
2: Easy Integration
The ease of integration is crucial for developers as it directly impacts the implementation timeline and overall development process. A 2FA tool that is easy to integrate can save time and resources. Here are the key aspects to consider:
Developer-Friendly APIs
Choose a 2FA tool that provides well-documented and easy-to-use APIs (Application Programming Interfaces). A good API simplifies the integration process, allowing developers to implement 2FA functionalities with minimal effort.
SDKs and Libraries
Look for 2FA solutions that offer software development kits (SDKs) or libraries for popular programming languages and frameworks. These tools can streamline integration and reduce the complexity of incorporating 2FA into your application.
Compatibility
Ensure that the 2FA tool is compatible with your existing technology stack. Whether your application is web-based, mobile, or both, the chosen tool should seamlessly integrate with your development environment.
Scalability
Consider the scalability of the 2FA solution to accommodate potential growth in user numbers. A tool that can scale easily will save you from future integration challenges as your application expands.
Selecting a 2FA vendor is like choosing a partner for a dance competition. Look for compatibility with your app, reliability, and cool moves (features).
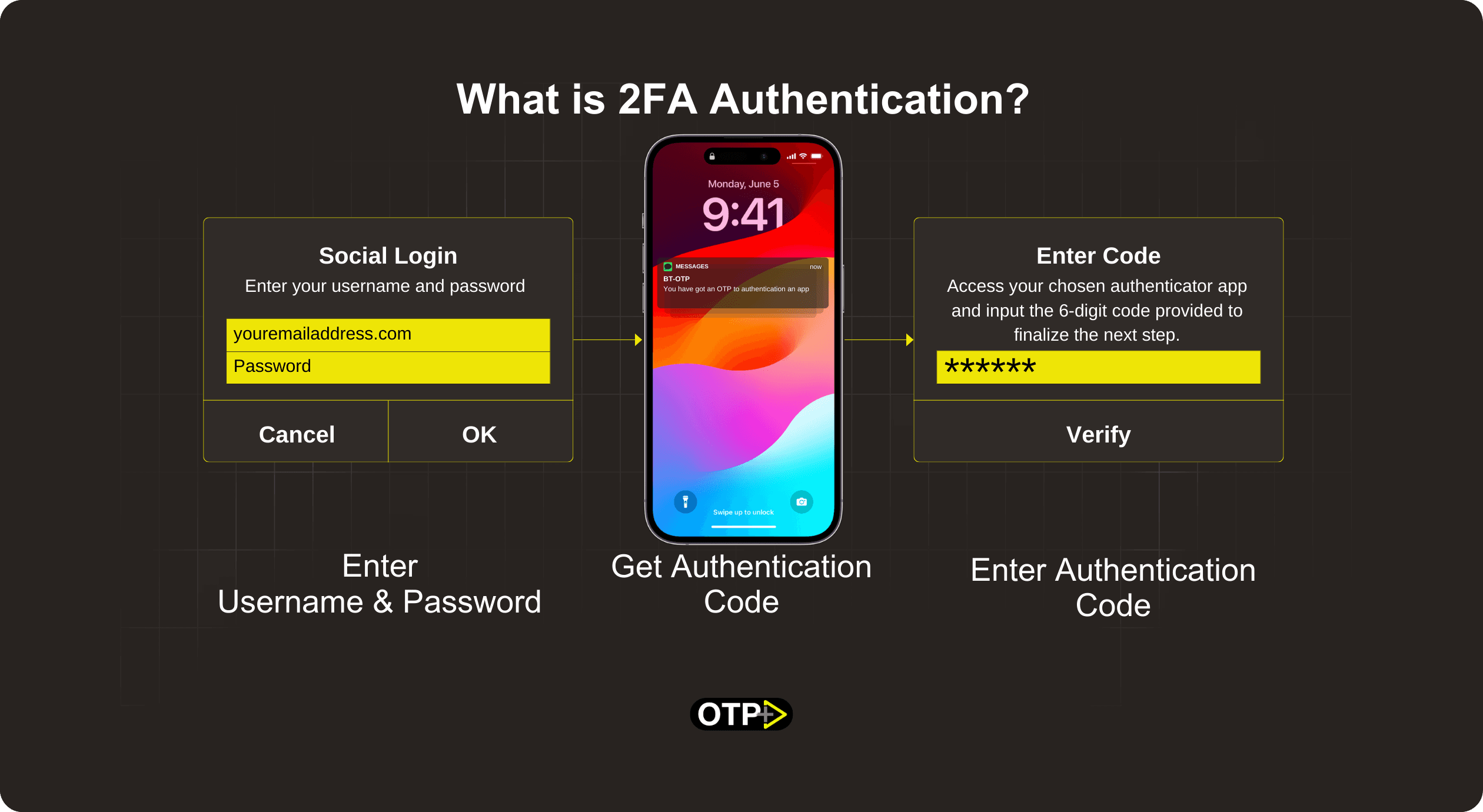
What is an Example of Two-Factor Authentication?
An example of two-factor authentication involves utilizing a combination of a password along with a one-time passcode sent to a mobile phone via SMS.
Picture this: You log in with your password, and then your phone buzzes with a special code. That code is your second superhero move – 2FA in action!
Pros and Cons of Two-Factor Authentication
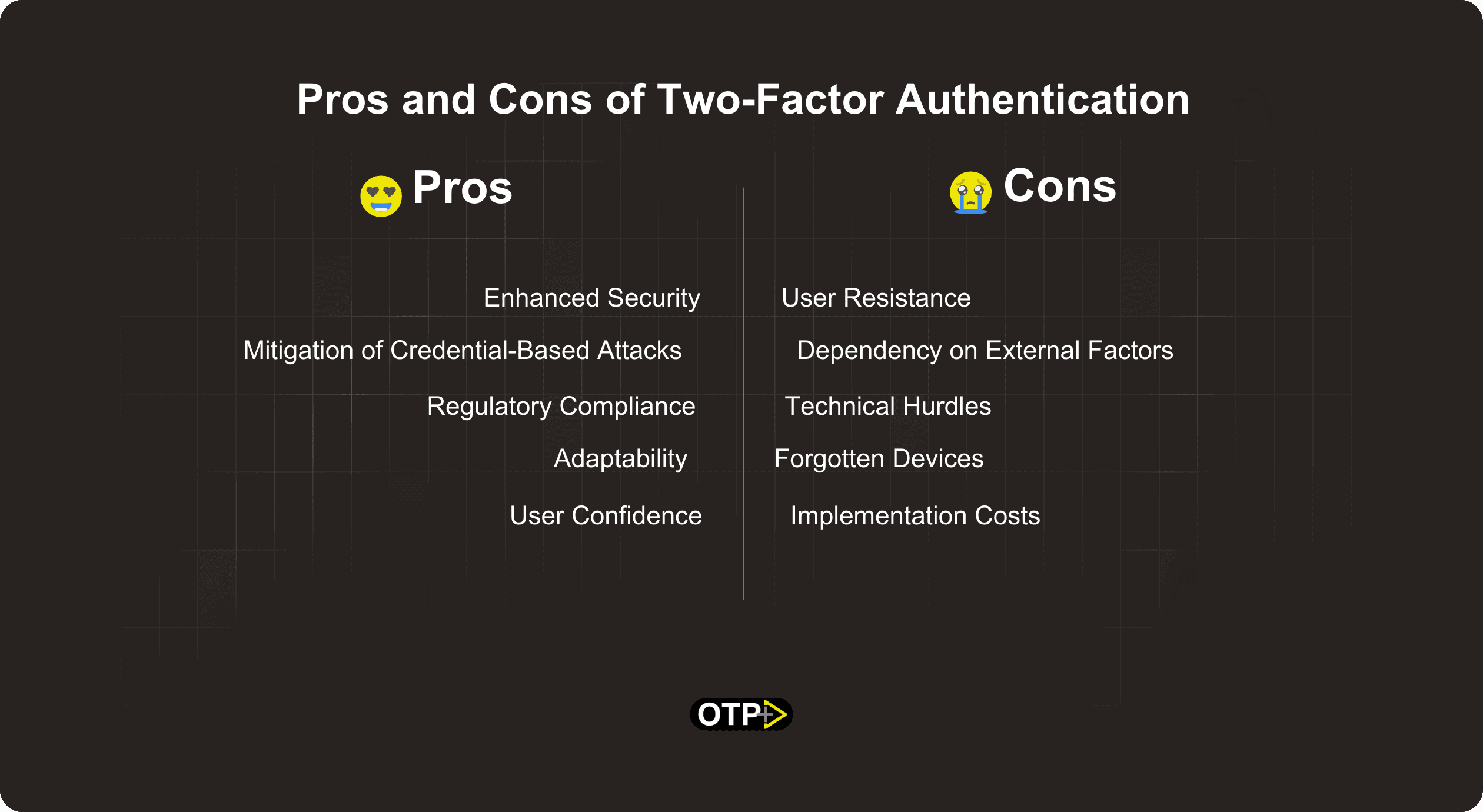
Pros
Enhanced Security
2FA adds an extra layer of defense, requiring two forms of verification for access, significantly reducing the risk of unauthorized entry.
Mitigation of Credential-Based Attacks
Traditional password-centric models are vulnerable to credential-based attacks. 2FA neutralizes this risk by demanding a second, distinct form of authentication.
Regulatory Compliance
In certain industries or for specific types of sensitive data, regulatory compliance like PCI DSS (Payment Card Industry Data Security Standard), Health Insurance Portability and Accountability Act (HIPAA), and General Data Protection Regulation (GDPR) mandates the use of 2FA as an additional security measure.
Adaptability
2FA methods vary, allowing businesses to choose authentication tools that best suit their needs, such as SMS codes, authenticator apps, or biometrics.
User Confidence
Users gain confidence in the security of their accounts, fostering trust and satisfaction with the platform or service.
Cons
User Resistance
Some users may find the additional step cumbersome, leading to resistance and potential reluctance to adopt 2FA.
Technical Hurdles
Implementing 2FA can pose technical challenges, including compatibility issues with existing systems and potential disruptions during the integration process.
Dependency on External Factors
Methods like SMS verification rely on external factors like network connectivity, which can be a drawback in areas with poor reception.
Forgotten Devices
Users might face challenges if they forget or lose the device used for the second factor, potentially leading to account lockouts.
Implementation Costs
Deploying 2FA may incur initial setup and maintenance costs, impacting smaller businesses or organizations with limited budgets.
Not Foolproof
While 2FA significantly enhances security, it is not completely foolproof. Advanced cyber threats may find ways to circumvent or exploit certain 2FA methods.
Does Two-Factor Authentication Prevent Hacking?

Absolutely! 2FA adds an extra layer of defense, making it much harder for hackers to break into your app. While 2FA is a robust security measure and significantly raises the bar for attackers, it is not foolproof.
Users and organizations should complement 2FA with other security practices, such as regular password updates, security awareness training, and monitoring for unusual account activities.
Additionally, choosing more secure 2FA methods, like app-based authenticators or hardware tokens, can enhance overall security.