Tips & Tricks
Authentication vs Authorization: Understanding the Basics
Vijay Kakadia
•
Mar 22, 2024
•
6
min read
Share
As we navigate the digital world, two essential concepts are crucial in keeping our online experiences safe and secure: Authentication and Authorization. In this blog post, we'll break down these terms, explore their differences in Authentication vs. Authorization, understand their factors, learn their techniques, and clear misconceptions about authentication and authorization. In a single line, Authentication verifies a user's identity, while authorization determines the access levels and permissions granted to that user.
To learn more in detail, let's start with the definition of authentication.
What is Authentication?
Definition: Authentication is confirming a user's or system's identity.
In simpler terms, it's like proving to the digital world that you are who you say you are. Imagine your password as the secret handshake that grants you access to your online accounts.
Example: When your user logs in to their email, it enters their username and password. If the system recognizes this combo, the user successfully authenticated themselves.
What is Authorization?
Definition: Authorization is granting or denying access to specific resources or actions.
Once you've proven your identity through authentication, authorization determines what you can or cannot do. It's like having different access levels—some doors are open, while others remain locked.
Example: Imagine you have a video streaming service. Once your user logs in (authentication), authorization kicks in to decide if the user has the right to watch premium content or is limited to the free section.
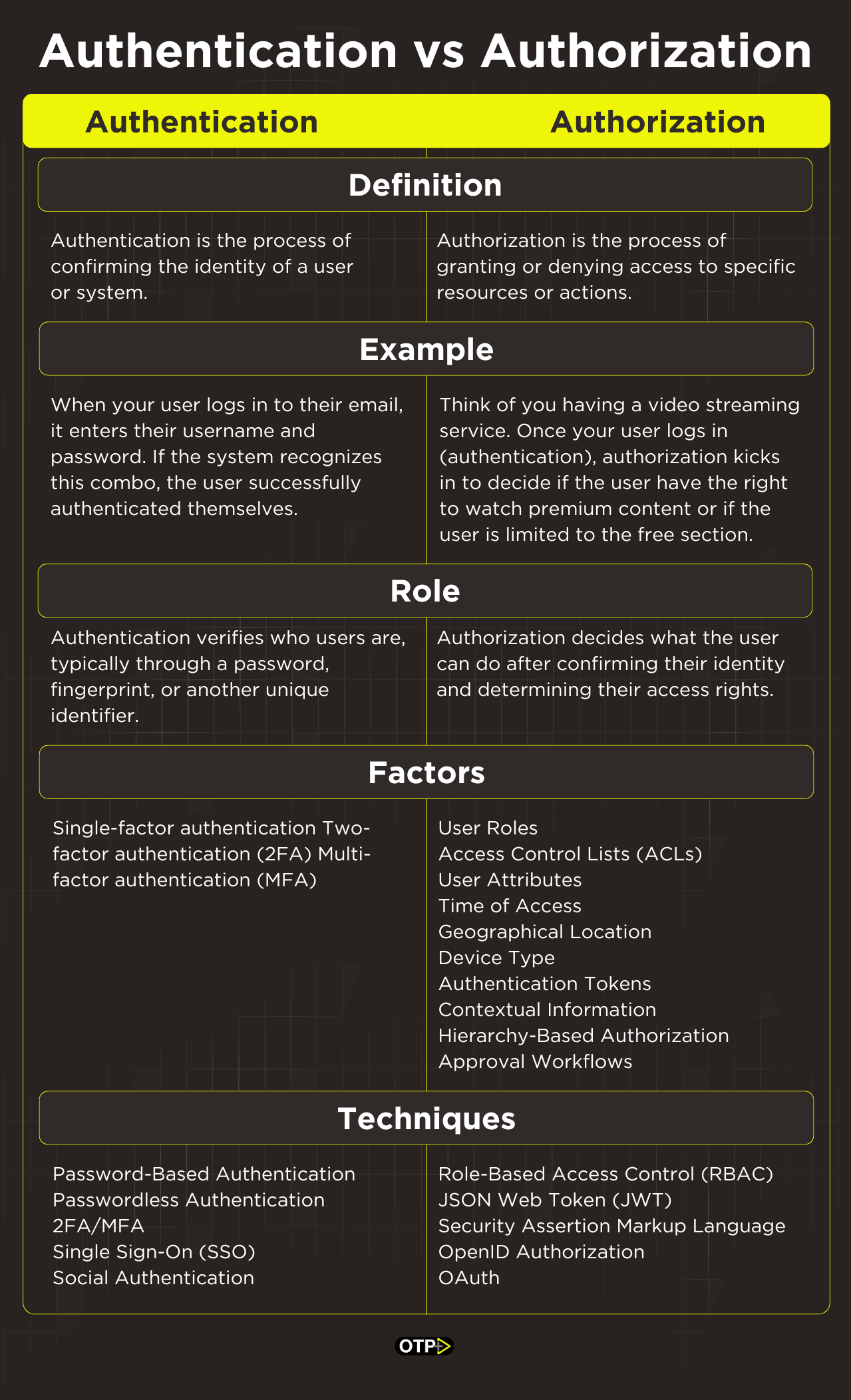
The Key Differences Between Authentication & Authorization
Authentication verifies who users are, typically through a password, fingerprint, or another unique identifier.
After confirming their identity and determining their access rights, authorization decides what the user can do.
Authentication Factors
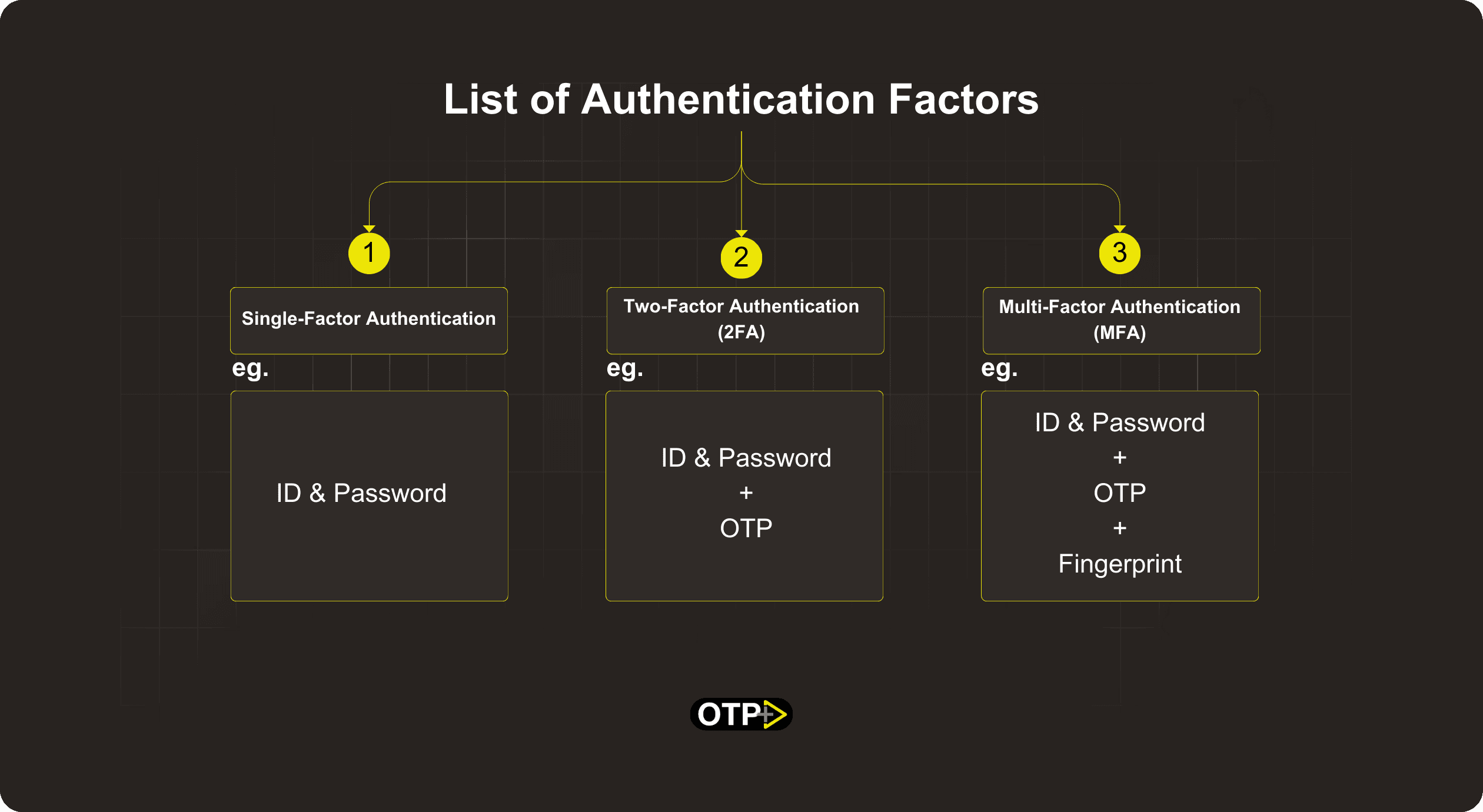
Single-factor authentication
Single-factor authentication relies on a single proof of identity, typically a password. It's like having one key to unlock the digital door.
Example: Imagine you are developing a fitness app where users only need to enter a password to access their workout routines and progress tracking. This is a classic example of Single-Factor Authentication, relying on a sole identifier.
Two-factor authentication (2FA)
Introducing an additional layer, Two-Factor Authentication requires users to provide two forms of identification. This could be a password and a one-time code sent to their mobile device.
Example: In a banking app, Two-Factor Authentication might involve users entering their password and receiving a time-sensitive code on their registered mobile device. This additional layer enhances security, ensuring that unauthorized access is thwarted even if passwords are compromised.
Multi-factor authentication (MFA)
Multi-factor authentication takes it up a notch by adding multiple layers of verification. This can include something the user knows (password), something the user has (like a security token), or something the user is (biometrics)
Example: Consider a healthcare app where users authenticate with a password and by scanning their fingerprints or entering a one-time code sent to their email. This multi-layered approach in Multi-Factor Authentication significantly raises the security bar.
Here is a detailed article that helps you to understand multifactor authentication with examples.
Authorization Factors
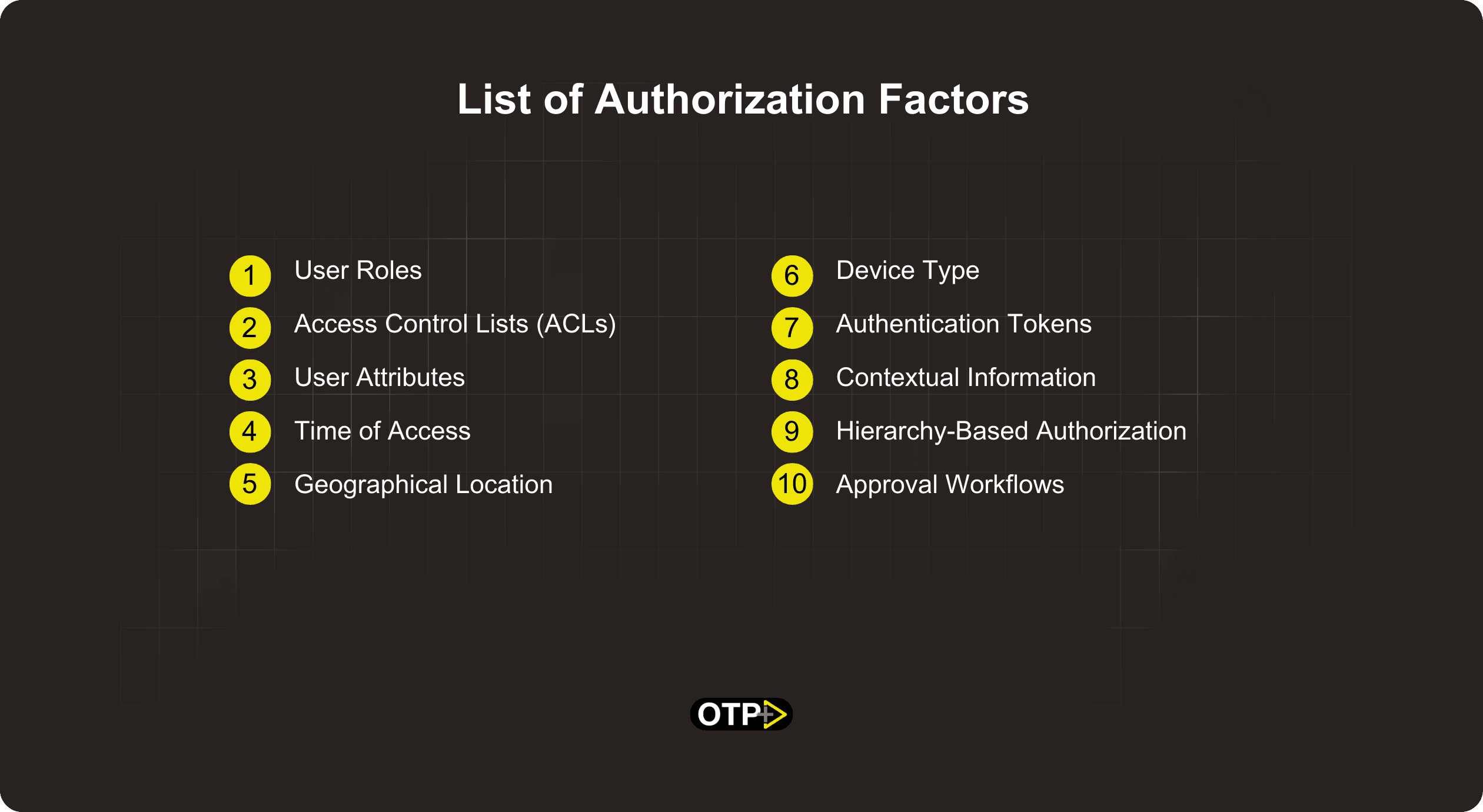
Once users have proven their identity through authentication, we move on to Authorization—determining what they can do within the application. Here are the authentication factors that allow users to access different functionalities of the app.
User Roles
Users are assigned specific roles within a system, each with predefined permissions.
Example: In a content management system, roles could include "Admin," "Editor," and "Viewer," each having different levels of access and capabilities.
Access Control Lists (ACLs)
Lists specify which users or system processes are granted access to objects and what operations are allowed on given objects.
Example: An ACL for a shared document may grant read and write permissions to specific users while restricting others' access.
User Attributes
Attributes or characteristics associated with a user account that influence access control decisions.
Example: A financial application might consider a user's account type (e.g., "Regular" or "Premium") to determine the level of financial data they can access.
Time of Access
Time of access specifies when a user is allowed or denied access to certain resources.
Example: A corporate network might restrict access to sensitive files during non-working hours.
Geographical Location
It controls access based on the physical location of the user.
Example: An e-commerce platform might limit access to certain features for users outside specific regions.
Device Type
Restricting access based on the type of device used by the user.
Example: An online banking app might offer limited functionality when accessed from a public computer compared to a trusted mobile device.
Authentication Tokens
Temporary tokens are obtained during the authentication process often used to access specific resources.
Example: After logging into a social media account, an authentication token allows the user to post updates without repeatedly entering their credentials.
Contextual Information
Contextual details such as user behavior, session history, or environmental factors are considered in access decisions.
Example: An e-learning platform might adjust access based on a user's learning progress or recent activity.
Hierarchy-Based Authorization
Determining access levels based on the organizational hierarchy or user's position.
Example: In a project management tool, higher-ranking team members may have broader access to project details than team members with lower roles.
Approval Workflows
At this point, authorization from higher authorities or administrators is required before granting specific access permissions.
Example: A document management system may require managerial approval before users access confidential files.
Now, let’s understand the techniques of Authentication and Authorization.
Authentication Techniques
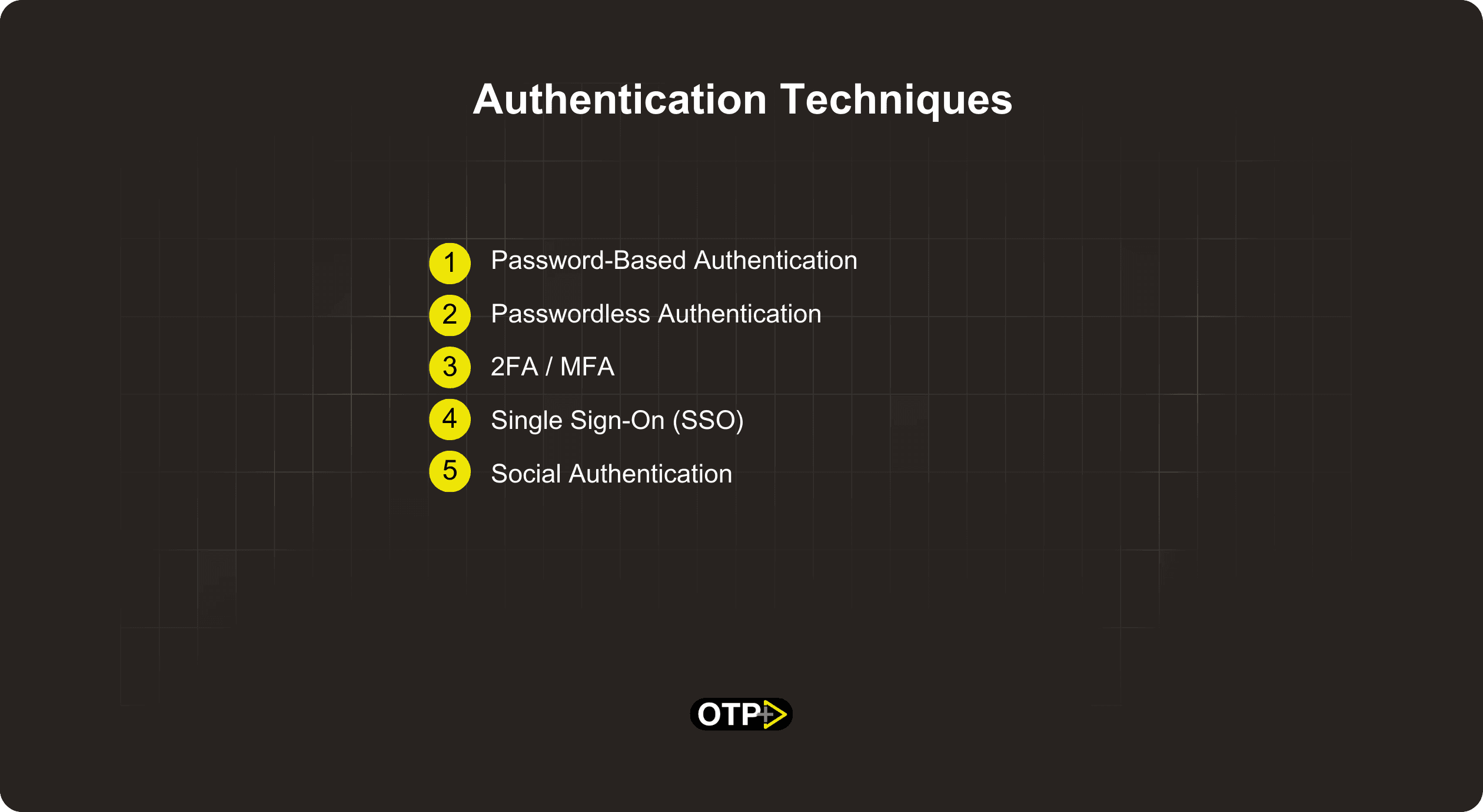
Password-Based Authentication
The classic method involves users entering a secure password. Ensuring robust password policies is crucial for this technique.
Example: In a messaging app, users log in with a robust and unique password. Ensuring that the password creation process includes complex requirements is crucial for the security of this technique.
Passwordless Authentication
Eliminating traditional passwords, this technique leverages alternative methods like biometrics or secure links sent via email.
Example: Consider a travel app where users can log in using facial recognition or a secure link sent to their email. This Passwordless Authentication method eliminates the reliance on traditional passwords, enhancing user convenience.
2FA/MFA
Implementing Two-Factor or Multi-Factor Authentication adds an extra layer of security, reducing the risk of unauthorized access.
Example: In a finance management app, implementing Two-Factor or Multi-Factor Authentication adds an extra layer of security. Users might authenticate with a password and then confirm their identity through a fingerprint scan or a code from an authentication app.
Single Sign-On (SSO)
SSO allows users to access multiple applications with a single set of credentials, enhancing user experience without compromising security.
Example: Imagine a suite of productivity apps where users sign in once and seamlessly gain access to email, calendar, and document editing tools. Single Sign-on simplifies the user experience without compromising security.
Social Authentication
Using social media credentials for authentication can simplify the user onboarding process, but it requires careful handling of user data.
Example: In a gaming app, users may sign up or log in using their social media credentials. While this accelerates onboarding, developers must carefully handle user data in compliance with privacy standards.
Authorization Techniques
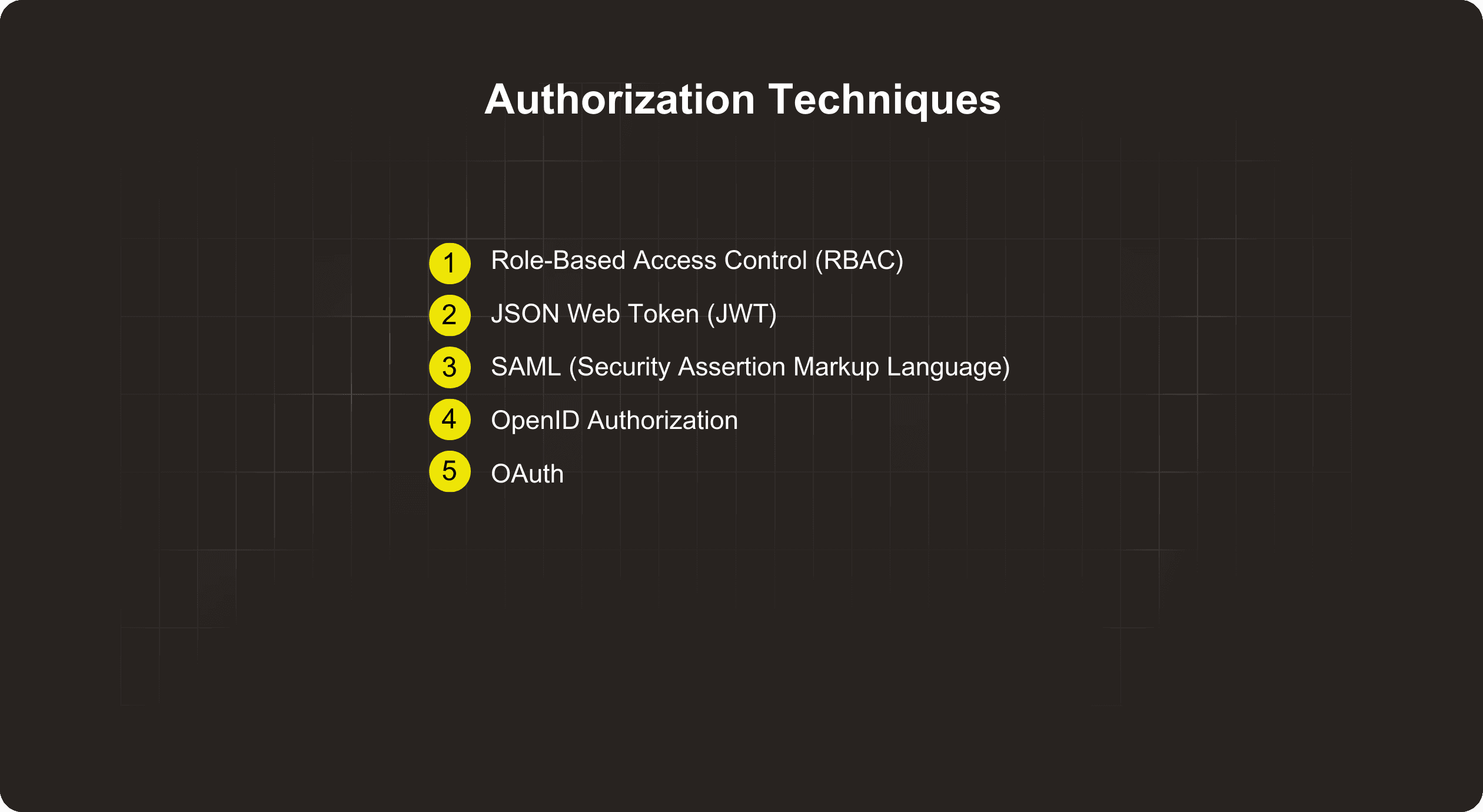
Role-Based Access Control (RBAC)
Assigning roles and permissions to users based on their responsibilities ensures a structured and secure access control system.
Example: Different team members may have varying access levels in a project management app. Role-based Access Control assigns roles like "Admin" or "Member," determining who can create projects, delegate tasks, or view sensitive data.
JSON Web Token (JWT)
JWTs are compact, URL-safe means of representing claims between two parties, providing a secure method for transmitting information.
Example: Consider an e-commerce app where a user logs in and upon successful authentication, receives a JWT. This token securely carries information about the user's role and permissions during subsequent interactions.
SAML (Security Assertion Markup Language)
SAML facilitates single sign-on and authentication and authorization data exchange between parties, promoting seamless interoperability.
Example: SAML facilitates secure access to various systems without repeatedly entering credentials in a corporate environment. Once authenticated, users can seamlessly navigate between interconnected applications.
OpenID Authorization
OpenID Connect enhances identity verification, providing a secure way for users to authorize third-party applications without sharing credentials.
Example: OpenID Connect allows users to log in using their Google or Facebook credentials in a blogging platform, streamlining the authorization process and enhancing user convenience.
OAuth
OAuth facilitates secure, delegated access to resources by allowing limited access tokens, ensuring users retain control over their data.
Example: Imagine a photo-sharing app where users can grant limited access to their photos for printing services. OAuth facilitates this secure, delegated access, ensuring users retain control over their data.
Why Authentication & Authorization Matters
Authentication and authorization work together. Even if someone cracks your password (authentication), they will only get far with the right permissions (authorization).
Common Misconceptions of Authentication & Authorization
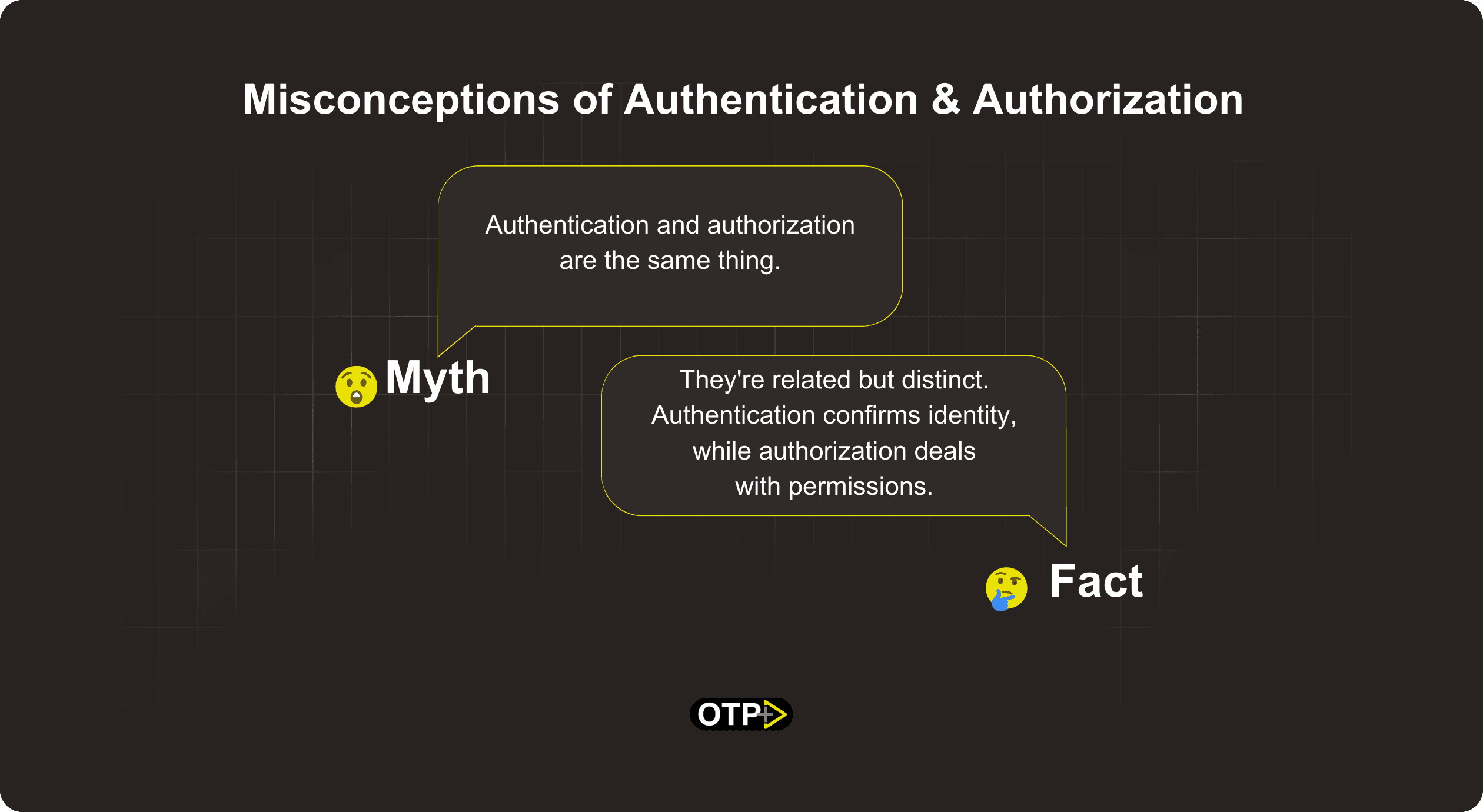
Myth: "Authentication and authorization are the same thing."
Fact: They're related but distinct. Authentication confirms identity, while authorization deals with permissions.
Wrap-up: Keeping Digital Spaces Safe
Understanding the dance between authentication and authorization is like having a digital superhero duo – one ensures you are who you claim to be. The other decides what powers (or access) you possess.
So, next time you log into your favorite app or website, remember the dynamic duo – Authentication vs Authorization – working behind the scenes to secure your digital adventures!