How To
2FA vs MFA: Which One You Should Use for Your App
Vijay Kakadia
•
Apr 9, 2024
•
5
min read
Share
As an app developer, ensuring the security of your application is paramount. In today's digital age, users expect their data to be safeguarded against threats. Two-factor authentication (2FA) and Multi-Factor Authentication (MFA) are essential tools for achieving this goal. In this guide, we'll explore the difference between 2FA vs MFA from a developer's perspective, empowering you to integrate robust security measures into your applications effectively.
What is Two-Factor Authentication (2FA)
2FA adds an extra layer of security to user authentication by requiring two different forms of verification before granting access. For developers, this typically means integrating mechanisms for verifying something the user knows (like a password) and something they have (such as a mobile device). Implementing 2FA strengthens your app's security posture by making it significantly harder for unauthorized users to gain access.
What is Multi-Factor Authentication (MFA)
MFA builds upon the foundation of 2FA by incorporating additional authentication factors beyond the traditional two. As a developer, this could involve integrating biometric scans, security tokens, or other forms of verification into your app's authentication process. By diversifying authentication methods, MFA provides an extra layer of defense against unauthorized access.
Key Differences: 2FA VS MFA
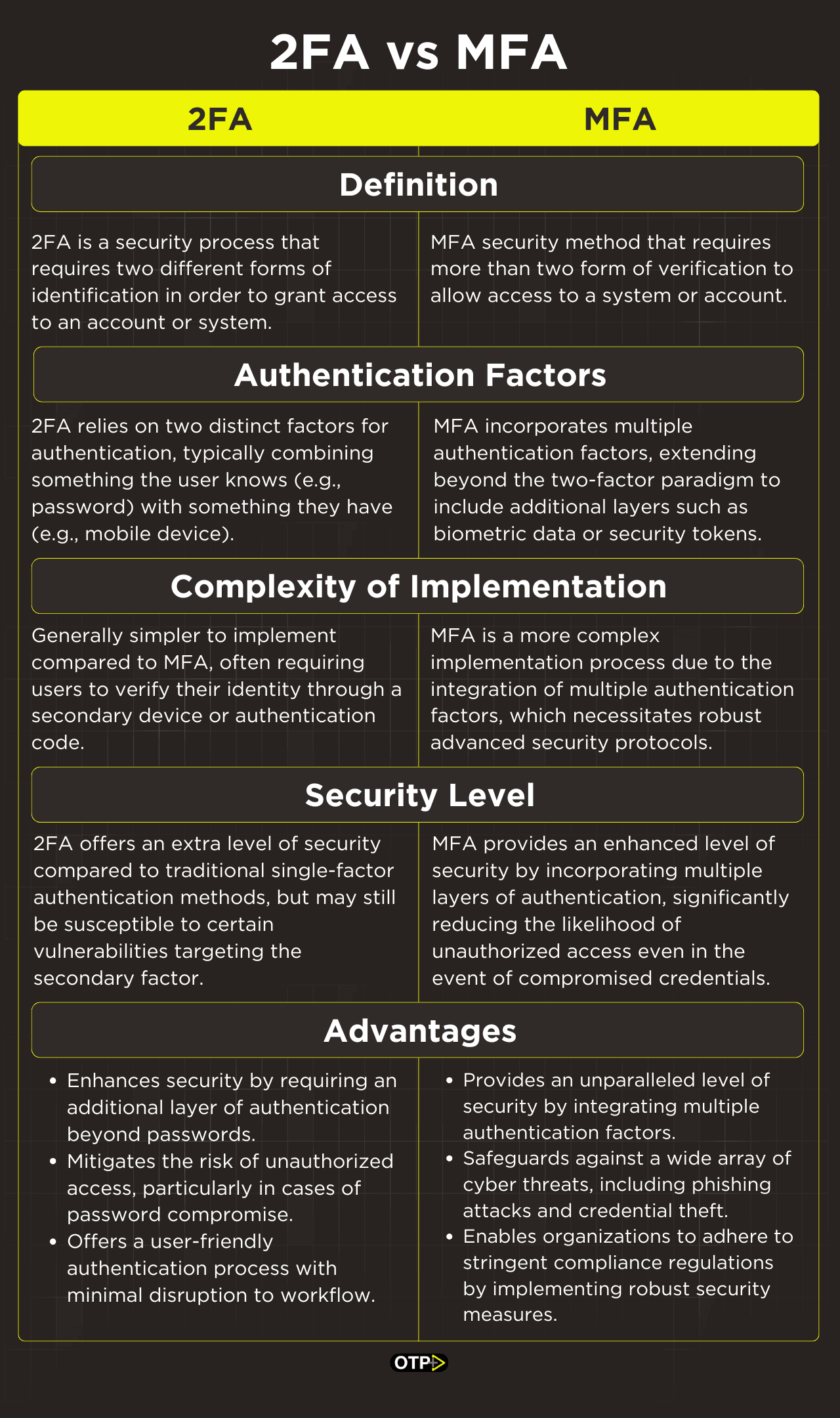
While both 2FA and MFA serve the overarching purpose of bolstering security, they differ in their approach and implementation.
Authentication Factors
2FA
2FA relies on two distinct factors for authentication, typically combining something the user knows (e.g., password) with something they have (e.g., mobile device).
MFA
MFA incorporates multiple authentication factors, extending beyond the two-factor paradigm to include additional layers such as biometric data or security tokens.
Complexity of Implementation
2FA
Generally simpler to implement compared to MFA, often requiring users to verify their identity through a secondary device or authentication code.
MFA
MFA is a more complex implementation process due to the integration of multiple authentication factors, which necessitates robust infrastructure and advanced security protocols.
Security Level
2FA
2FA offers an elevated level of security compared to traditional single-factor authentication methods, but may still be susceptible to certain vulnerabilities such as phishing attacks targeting the secondary factor.
MFA
MFA provides an enhanced level of security by incorporating multiple layers of authentication, significantly reducing the likelihood of unauthorized access even in the event of compromised credentials.
Implementation Advantages 2FA VS MFA
2FA Advantages
Enhances security by requiring an additional layer of authentication beyond passwords.
Mitigates the risk of unauthorized access, particularly in cases of password compromise.
Offers a user-friendly authentication process with minimal disruption to workflow.
MFA Advantages
Provides an unparalleled level of security by integrating multiple authentication factors.
Safeguards against a wide array of cyber threats, including phishing attacks and credential theft.
Enables organizations to adhere to stringent compliance regulations by implementing robust security measures.
Implementation Best Practices of 2FA and MFA
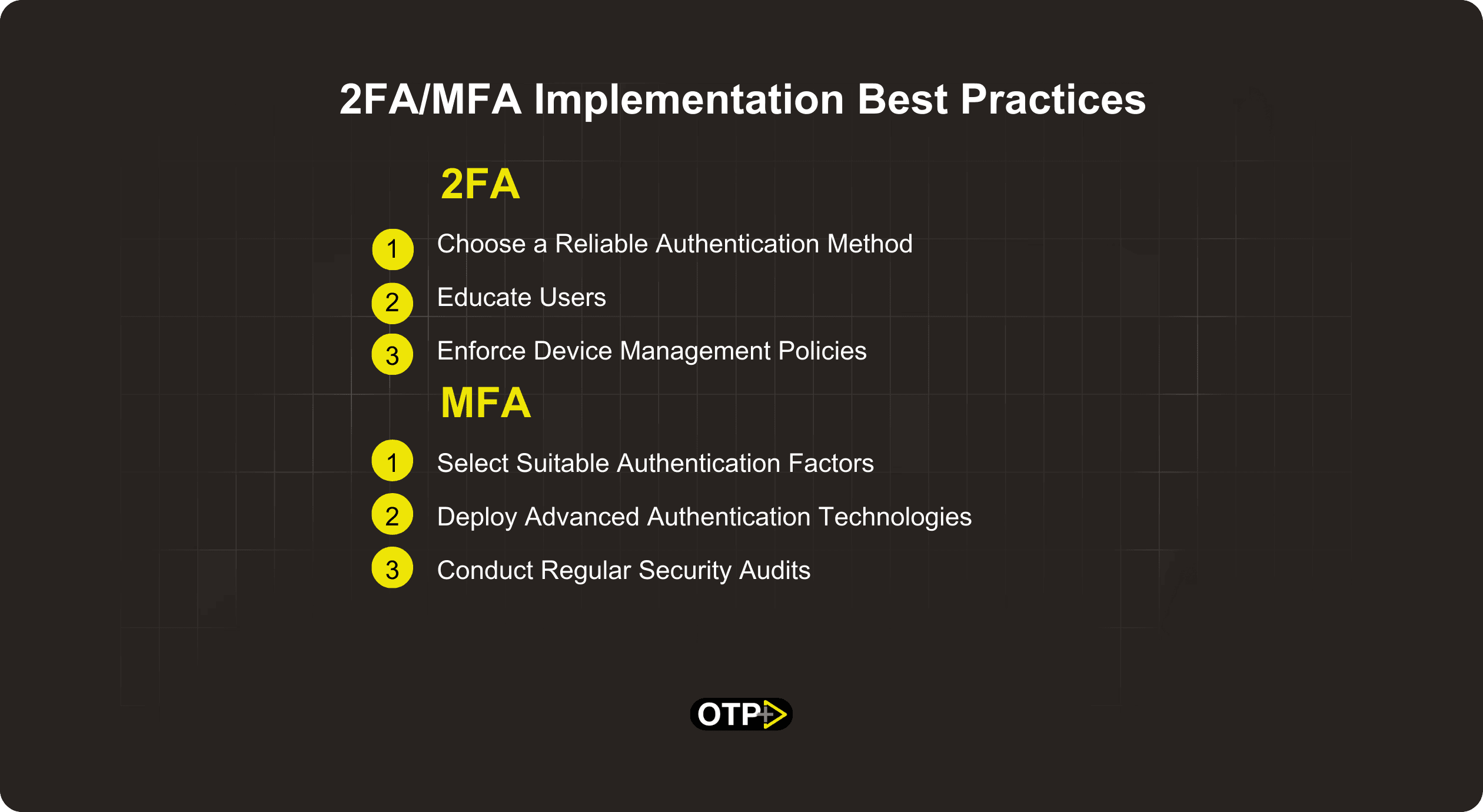
2FA Implementation Best Practices
Choose a Reliable Authentication Method
Opt for reputable 2FA solutions that offer a seamless user experience and robust security features.
Educate Users
Provide comprehensive training and resources to educate users on the importance of 2FA and best practices for implementation.
Enforce Device Management Policies
Implement policies to manage authorized devices and ensure secure access to sensitive information.
MFA Implementation Best Practices
Select Suitable Authentication Factors
Evaluate the specific security needs of your organization and choose MFA factors that align with your risk profile.
Deploy Advanced Authentication Technologies
Leverage cutting-edge authentication technologies such as biometrics and behavioral analytics to enhance security posture.
Conduct Regular Security Audits
Regularly assess and audit your MFA implementation to identify vulnerabilities and address any potential security gaps.
Conclusion
In conclusion, Two-Factor Authentication (2FA) and Multi-Factor Authentication (MFA) play pivotal roles in safeguarding digital assets against evolving cyber threats. While 2FA provides an additional layer of security through dual-factor authentication, MFA elevates security posture by integrating multiple authentication factors. By understanding the key differences and advantages of these authentication methods, organizations can fortify their defenses and mitigate the risk of unauthorized access to sensitive information.
By adhering to best practices and embracing a holistic approach to authentication, businesses can ensure robust security measures that withstand the ever-evolving threat landscape.