Defending your future
Empowering businesses with cutting-edge cybersecurity solutions and unbreakable defences.
Empowering the most exceptional product teams globally, spanning from emerging startups to well-established enterprises.
Comprehensive Security Solutions
We specialise in providing top-notch solutions for businesses of all sizes.
Encryption with Dash
The gap is closing between with Spark, and for everyone to be successful from attacks.
Zero Trust Network Access
ZTNA is a cloud-based solution that ensures streamlined access to data and applications.
Trusted global presence
Spark provides service from redundant cloud regions to high-bandwidth connectivity areas.
Advanced permissions controls
With Spark, easily manage permission controls straight from app.
International standards of security
We follow internationals standards of security measures to keep clients our secure.

Cloud Security
Ensure secure cloud infrastructure against vulnerabilities

Firewall Protection
Safeguard your network from unauthorized access

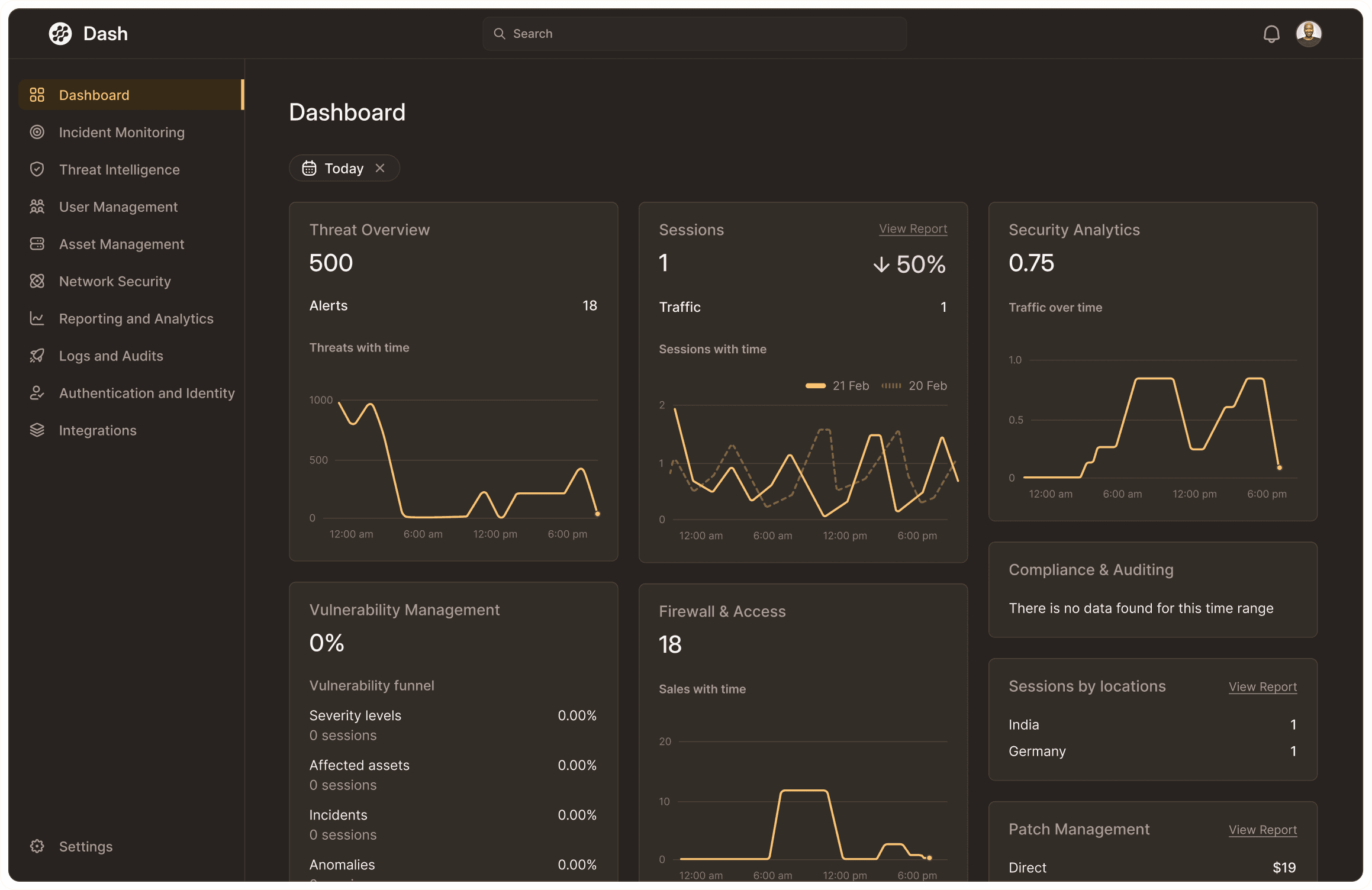
Security Dashboard
Gain insights through a user-friendly dashboard

Secure File Transfer
Manage permissions for file access and sharing

Mobile Device Management
Securely erase data from lost or stolen devices

Threat Intelligence Feeds
Stay informed about global threats and trends
At Big Company, our security transformed with Dash. With real-time threat insights, user-friendly controls, and robust incident response, Spark empowers our team to safeguard our digital landscape effectively.

Kristin Watson
CEO, Big Company
Dash's cutting-edge technology exceeded our expectations. Its adaptive features and continuous updates ensure we stay ahead of cyber threats. An invaluable asset for any organization serious about security.

Cody Fisher
Bank of America
At our enterprise scale, cybersecurity is paramount. Spark has proven to be an indispensable asset in safeguarding our digital infrastructure. Its robust threat analysis, real-time incident response, and user-friendly interface make it an ideal solution.

Floyd Miles
Product support, Face
Dash cybersecurity platform delivers robust protection. Real-time threat detection and swift response make it indispensable for securing our network. Highly recommend for peace of mind!

Brooklyn Simmons
eBay
At Big Company, our security transformed with Spark. With real-time threat insights, user-friendly controls, and robust incident response, Spark empowers our team to safeguard our digital landscape effectively.

Ralph Edwards
Ferrari
Everything you need to know about Dash platform