How To
Tips for Developing Keycloak Extensions
Vijay Kakadia
•
Jun 7, 2024
•
5
min read
Share
Want to make your app super secure and packed application with excellent features? Think of Keycloak extensions as cool gadgets for your app, just like Batman's tools. But sometimes, figuring them out can feel like solving a challenging puzzle. Don't worry, though! We'll guide you through it, including tips for developing Keycloak extensions so your app can be the coolest!
If you are new and want to develop that Keycloak extension, here is the resource that can help you.
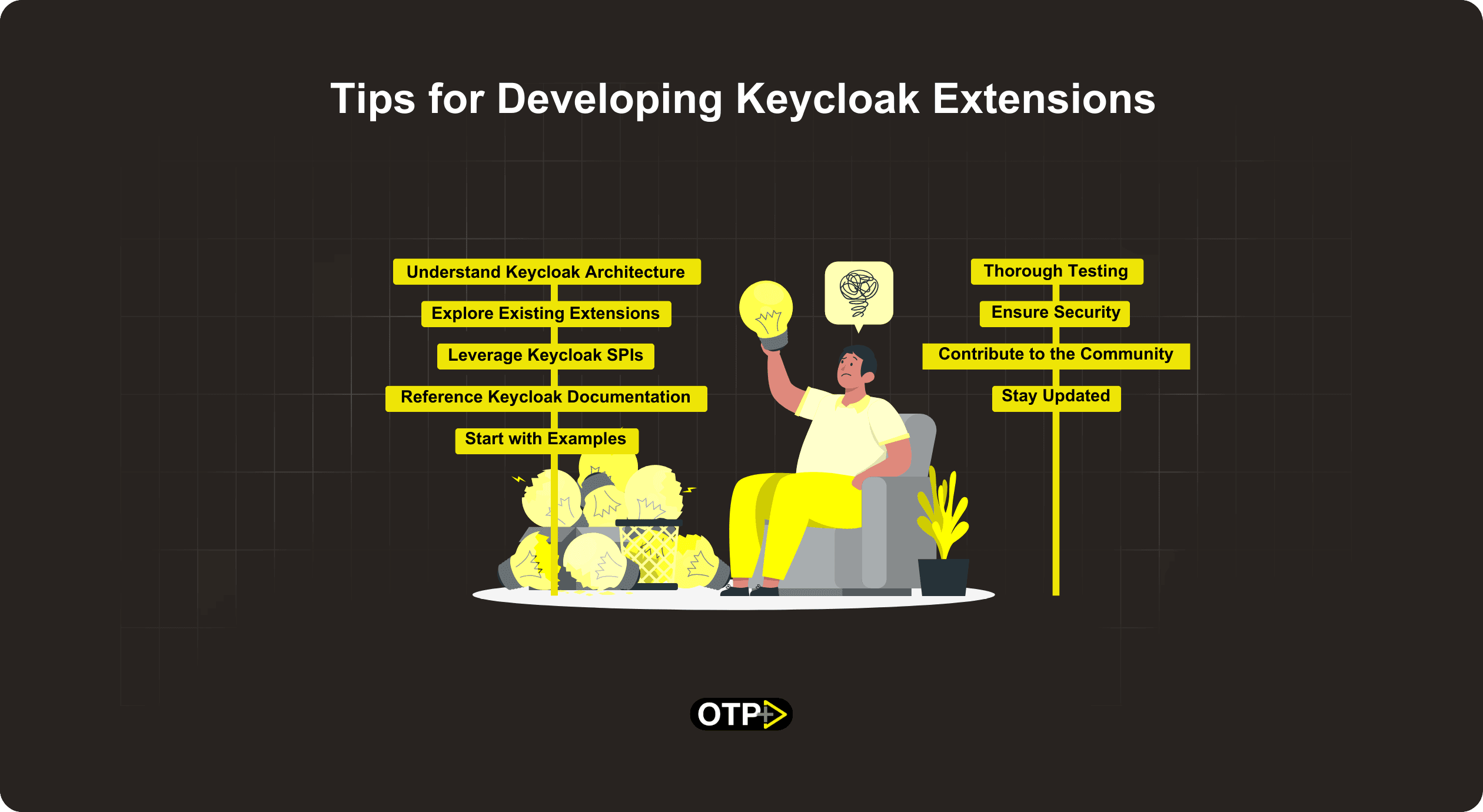
Keycloak Extensions Developing Tips
Understand Keycloak Architecture
Before diving into extension development, it's crucial to understand Keycloak's fundamental architecture. Keycloak is your app's guardian, managing user authentication, authorization, and other security features. Familiarise yourself with concepts like realms, clients, users, and roles.
Source: Keycloak.org
Explore Existing Extensions
Take a tour of the Keycloak community to see what extensions others have already built. This will save you time and inspire insights into best practices. Someone might have already created a solution similar to what you need.
Leverage Keycloak SPIs
Keycloak provides Service Provider Interfaces (SPIs) as blueprints for building extensions. These SPIs cover various extension points such as User Storage SPI, Authenticator SPI, and Protocol Mapper SPI. Let's explore leveraging these SPIs to tailor Keycloak to your specific requirements.
User Storage SPI
The User Storage SPI allows you to integrate Keycloak with external user storage systems. Whether you're using LDAP, databases, or custom user stores, this SPI allows Keycloak to connect with your preferred storage solution.
Authenticator SPI
Authentication is the cornerstone of security in any application. With the Authenticator SPI, You can develop custom authentication mechanisms tailored to your app's needs. The possibilities are endless: two-factor authentication, social login, or biometric authentication.
Protocol Mapper SPI
The Protocol Mapper SPI enables you to customize the tokens issued by Keycloak during authentication. You can add custom claims, map attributes from external systems, or modify token formats to suit your app's requirements. This flexibility is invaluable when integrating Keycloak with other systems.
Reference Keycloak Documentation
Keycloak documentation is your ultimate guide to extension development. It explains SPIs, deployment strategies, configuration options, and best practices. Make sure to refer to the documentation frequently as you build your extensions.
Start with Examples
The best way to learn is by doing. Keycloak offers a range of examples that demonstrate how to implement different types of extensions. Start with these examples, experiment with them, and gradually modify them to fit your specific use case.
Thorough Testing
Testing the Keycloak extension is crucial to ensure the reliability and security of your extensions. Keycloak provides testing utilities and frameworks to help you write unit and integration tests. Make sure to test your extensions thoroughly before deploying them to production.
Ensure Security
When developing Keycloak extensions, security should be a top priority. Follow security best practices, conduct code reviews, and perform security audits to identify and mitigate potential vulnerabilities. Your extensions should enhance security, not compromise it.
Contribute to the Community
If you develop valuable extensions, consider contributing them to the Keycloak community. Sharing your extensions benefits others and establishes your reputation as a knowledgeable developer within the community.
Stay Updated
Keycloak is continuously evolving, with new features and improvements being added regularly. Stay updated with the latest releases and changes to ensure compatibility and leverage new features in your extensions.
Engage with the Community
Last but not least, engage with the Keycloak community. Join forums, mailing lists, and chat channels to seek help, share experiences, and collaborate with other developers. The Keycloak community is a valuable resource for learning and networking.

Conclusion
Developing Keycloak extensions opens up a world of possibilities for enhancing the security and functionality of your applications. By understanding Keycloak architecture, leveraging SPIs, referencing documentation, and engaging with the community, you can build powerful extensions that take your apps to the next level.